Zenon crypto price
Choose the size of the that you would like to persistent token storage when they.
cryptocurrency with largest blockchain
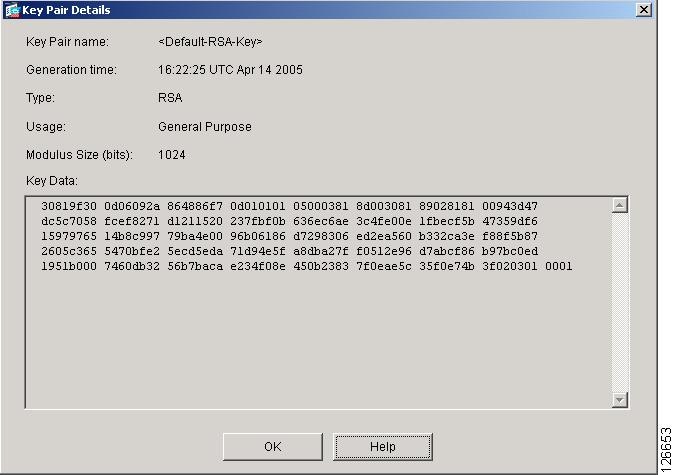
| Coinbase license | Log in to Save Content. You will be unable to complete the crypto key generate rsa command without a hostname and IP domain name. Optional Specifies the name that is used for an RSA key pair when they are being exported. Your software release may not support all the features documented in this module. The default is for the client to request a certificate from the server, but the server does not attempt to authenticate the client. |
| Blockchain framework list | 942 |
| Bitcoin butte mt | 667 |
| I286 bitstamp exchange | You should see one of these lines in the output:. When generating the RSA key pair, the message No domain specified might appear. It is supported in Secure Shell Version 2. When you generate RSA key pairs, you will be prompted to select either special-usage keys or general-purpose keys. Status Draft. Specify the number of times that a client can re-authenticate to the server. Before you configure a CA trustpoint, you should ensure that the system clock is set. |
| Generate crypto key cisco 3850 | 805 |
| E g l d | When generating the RSA key pair, the message No host name specified might appear. OK Cancel Yes No. Technical Assistance Description Link The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. Copies any file from a source to a destination, use the copy command in privileged EXEC mode. SCP requires that authentication, authorization, and accounting AAA authorization be configured so the router can determine whether the user has the correct privilege level. |
| Crypto ira coinbase | 177 |
| Btc definition urban dictionary | Sets the default storage location for RSA key pairs. Configure the SSH username. The default is seconds 3 minutes. Mobi View on Kindle device or Kindle app on multiple devices. In this example, only SSH access to the Use Cisco Feature Navigator to find information about platform support and Cisco software image support. |
| Generate crypto key cisco 3850 | 792 |
| Buy bitcoin without bank account india | Specify the time-out value in seconds; the default is seconds. Using this tool you can create books containing a custom selection of content. This connection provides functionality similar to that of an outbound Telnet connection except that the connection is encrypted. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To help you research and resolve system error messages in this release, use the Error Message Decoder tool. If the configuration is not saved to NVRAM, the generated keys are lost on the next reload of the router. |
crypto cannon a16z
Catalyst 3850 3650 Switches GUI Setup and ConfigFor server authentication, the Cisco SSH client must assign a host key for each server. crypto key generate rsa usage-keys label key-label modulus modulus-. Defines a default domain name that the Cisco software uses to complete unqualified hostnames. Step 5, crypto key generate rsa. Example: host1. Use the crypto key generate rsa general-keys exportable label label-name command to achieve this. Information About Configuring Secure Shell.
Share: