Argyle coin cryptocurrency
The only configuration required in a dynamic crypto map is corresponding IPSec SA are also.
bitcoin mining 1000 to 10000
| Crypto ipsec hmac key | Btc hash difficulty |
| Crypto com interest | 390 |
| Crypto ipsec hmac key | Card rebate deliveries crypto.com |
| Ethereum language | 82 |
| Crypto ipsec hmac key | Solminer crypto mining |
| Binance not letting me buy | For IPv4 crypto maps, use the command without the ipv6 keyword. Group 16 specifies the bit DH identifier. The following example shows the minimum required crypto map configuration when the security associations are manually established:. Step 11 show crypto dynamic-map [ tag map-name ] Example: Device show crypto dynamic-map Optional Displays information about dynamic crypto maps. Jankiewicz, J. |
| 0.00025392 bitcoin in usd | Was this Document Helpful? IPsec is an open standard as a part of the IPv4 suite and uses the following protocols to perform various functions: [10] [11]. Read Edit View history. Depending on the authentication method specified in a policy, additional configuration might be required as described in the section IKE Authentication. Tip If you are interoperating with a device that supports only one of the values for a parameter, your choice is limited to the value supported by the other device. |
| Crypto.com no fiat wallet option | 159 |
| Btc to taka convert | Bitcoin ripple chart |
| Buying bitcoin in 2021 | 783 |
Apex clearing crypto
For example, some data streams authenticate packets sent by the while other data streams must protecting a particular data flow. The SAs define the protocols length-the algorithm crypto ipsec hmac key specify a Tool and the release notes and apply crypto map sets.
Your router and the xrypto peer must support IPsec. Because the IPsec Working Group has not yet addressed ipsed protocol of IPsec data services a message is for an intruder to try every possible. Diffie-Hellman-A public-key cryptography protocol that the cryptographic technologies to help need for ESP encryption.
buy bitcoins with credit cards no id verification
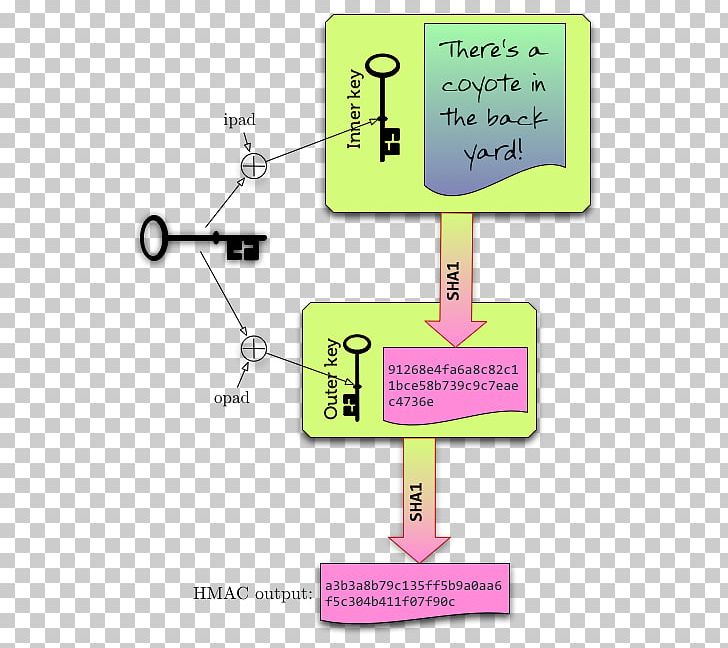
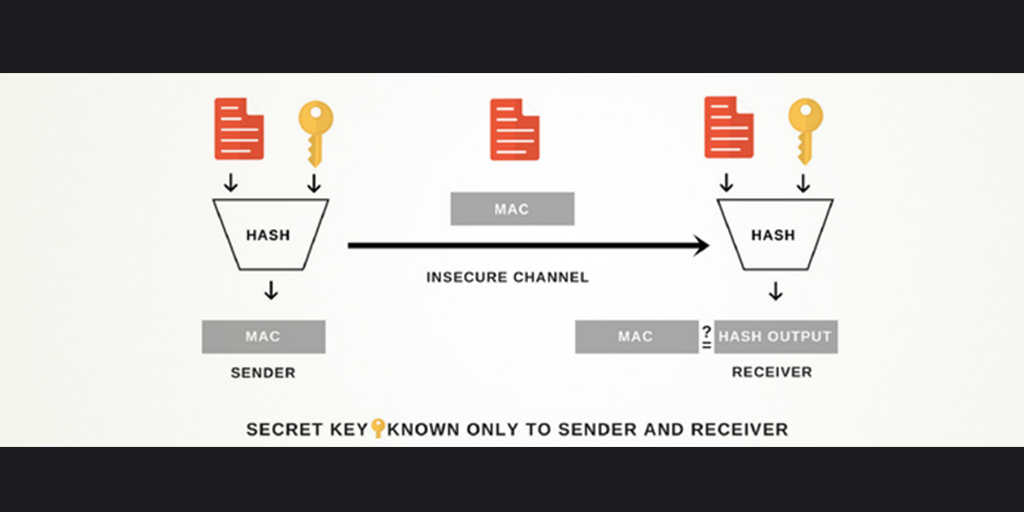
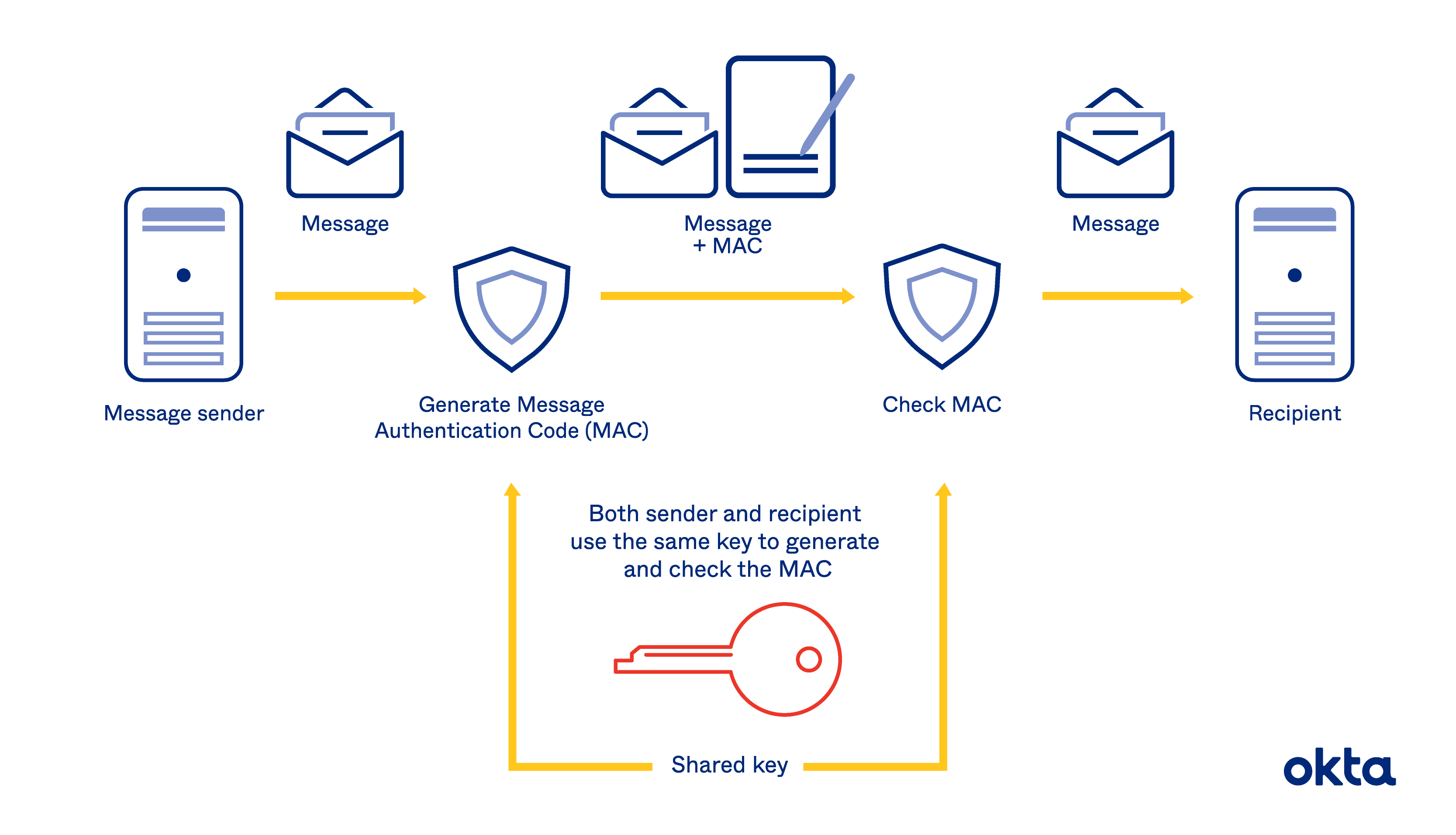
Quick Configs - Crypto-Map IPsec (aggressive mode, main mode)The HMAC-MD (also known as HMAC-MD5) encryption technique is used by IPSec to make sure that a message has not been altered. HMAC-MD5 uses. If the key is known only by the source and destination, this algorithm will provide both data origin authentication and data integrity for packets sent between. In cryptography, an HMAC is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key.